On testing the popular WordPress testimonials plugin, Strong Testimonials, I found multiple stored XSS vulnerabilities in the plugin. All WordPress websites using Strong Testimonials version 2.40.0 and below are affected.
Summary
Strong Testimonials is a popular and easily customizable WordPress testimonial plugin with over 90,000 active installations. The stored XSS vulnerability found in the plugin can be exploited by attackers to perform malicious actions such as stealing the victim’s session cookies or login credentials, performing arbitrary actions on the victim’s behalf, logging their keystrokes and more.
Vulnerability
In the client details section which is seen when adding or editing a testimonial, the custom[client_name] and custom[company_name] parameters were found to be vulnerable to stored cross-site scripting.
When the testimonial is added to a page on the site, the XSS payload passed in both of the above mentioned vulnerable parameters get executed.
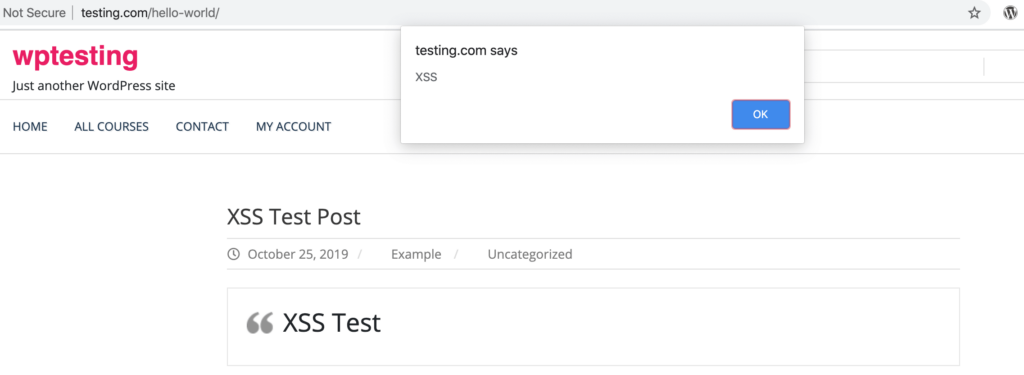
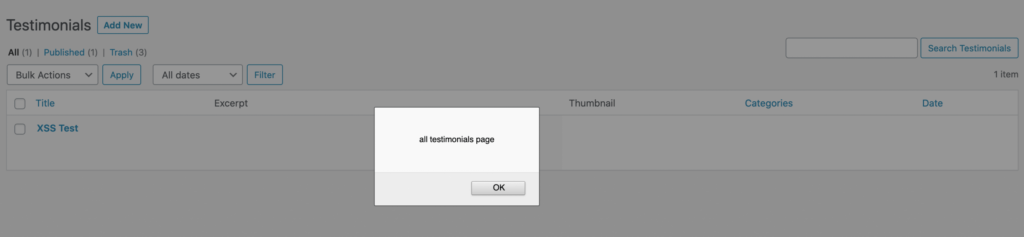
The payload in custom[client_name] also gets executed in the All Testimonials (/wp-admin/edit.php?post_type=wpm-testimonial) page.
Timeline
- Vulnerability reported to the Strong Testimonials team – January 23, 2020
- Strong Testimonials version 2.40.1 containing the fix released – January 25, 2020
Recommendation
It is highly recommended to update the plugin to the latest version.





