One of the first things you do when auditing a WordPress website is checking for ways to enumerate the admin username. In cases where the admin username is revealed, it’s pretty common to see the WordPress login page taking a large number of hits from brute force attacks against that username.
In this article, I will talk about some common attacks used by hackers and some measures you can take to prevent Username Enumeration in WordPress.
Common Attacks
The common methods deployed by hackers when attempting username enumeration in WordPress are:
1. Author Archives
If permalinks are enabled, in many WordPress installations it is possible to enumerate all the WordPress usernames iterating through the author archives. Whenever a post is published, the username or alias is shown as the author. For example, the URL http://site.com/?author=1 will show all the posts from user id 1. Attackers can abuse this functionality to figure out which usernames are available on the site.
— Acunetix
In this attack, hackers add author=n to the website URL, as shown below.
https://domain.com/?author=1
The request will be redirected to the author’s page with the corresponding user ID.
https://domain.com/author/admin_username
Note: The ID 1 usually represents the admin.
2. REST API
WordPress includes a REST API that can be used to list the information about the registered users on a WordPress installation. The REST API exposed user data for all users who had authored a post of a public post type. WordPress 4.7.1 limits this to only post types which have specified that they should be shown within the REST API.
— Acunetix
In this attack, hackers access the WordPress domain by adding /wp-json/wp/v2/users to the end of the URL, as shown below.
https://domain.com/wp-json/wp/v2/users
It outputs something like the following:
[{
"id":1,
"name":"admin",
"url":"",
"description":"",
"link":"http:\/\/...\/author\/admin\/",
"slug":"admin",
"avatar_urls":{
"24":"http:\/\/1.gravatar.com\/avatar\/...",
"48":"http:\/\/1.gravatar.com\/avatar\/...",
"96":"http:\/\/1.gravatar.com\/avatar\/..."
},
"meta":[
],
"_links":{
"self":[
{
"href":"http:\/\/.../wp-json\/wp\/v2\/users\/1"
}
],
"collection":[
{
"href":"http:\/\/..."
}
]
}
},...As can be seen here, the username and ID are visible to the hacker.
3. WPintel
Another rather easier method is to install the chrome extension WPintel which can enumerate the WordPress usernames for you by exploiting the REST API vulnerability discussed above.

Preventing WordPress Username Enumeration
Some of the common fixes used to prevent WordPress Enumeration are listed below:
1. .htaccess code to block all author scans
# BEGIN block author scans
RewriteEngine On
RewriteBase /
RewriteCond %{QUERY_STRING} (author=\d+) [NC]
RewriteRule .* - [F]
# END block author scans
Adding the above code to the .htaccess file in your WordPress website‘s root directory will block all author scan attacks discussed above.
2. Installing WordPress plugins
Plugins such as WP-Hardening, Disable REST API and Stop User Enumeration are some that help mitigate this vulnerability. However, in certain situations where the REST API needs to be enabled, this could be a problem.
As such, combining the above method and the below method is my preferred solution to this vulnerability.
3. Masking Usernames via Database
In addition to adding the above .htaccess code to block author scans, the usernames revealed through REST API vulnerability by direct URL access or using a plugin like WPintel can be masked in such a way that the actual username will not be displayed, but a random string chosen by you. Follow the below steps to implement this fix.
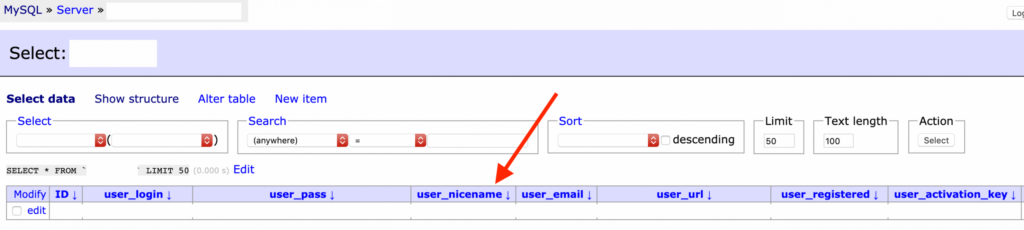
- Access the database.
- Select the table wp_users, or in case you have changed the wp- table prefix, then select [your-prefix]_users table.
- In the selected table, you will find a column named user_nicename. For each of the user accounts whose username you want to mask, change its respective user_nicename value to something random. The value you choose will be the one displayed when hackers perform any of the above-listed username enumeration attacks.
Conclusion
And there you go. These are some of the fixes available for WordPress Username Enumeration attacks. Hope this helps! 🙂
Hope you enjoyed the read!
You can follow me on Medium for more stories about the various Security Audits I do and the crazy vulnerabilities I find, as well as on Twitter for more Cybersecurity related news.