While performing a security audit on one of our client’s website, I discovered a reflected cross-site scripting (XSS) vulnerability in the WordPress LMS plugin by LearnDash. All WordPress websites using LearnDash version 3.0.0 through 3.1.1 are affected.
Summary
LearnDash is one of the most popular and easiest to use WordPress LMS plugins on the market. It allows users to easily create courses and sell them online and boasts a large customer base. The XSS vulnerability in LearnDash can be exploited by attackers against authenticated users to perform malicious actions such as stealing the victim’s session cookies or login credentials, performing arbitrary actions on the victim’s behalf, logging their keystrokes and more.
Vulnerability
Once the user is logged in to the WordPress website where the vulnerable LearnDash plugin is installed, the XSS payload can be inserted into the Search Your Courses box. The payload gets executed because the user input is not properly validated.
As a result, passing the XSS payload as a query string in the URL will also execute the payload.
[wordpress website][learndash my-account page]?ld-profile-search=%3Cscript%3Ealert(document.cookie)%3C/script%3E
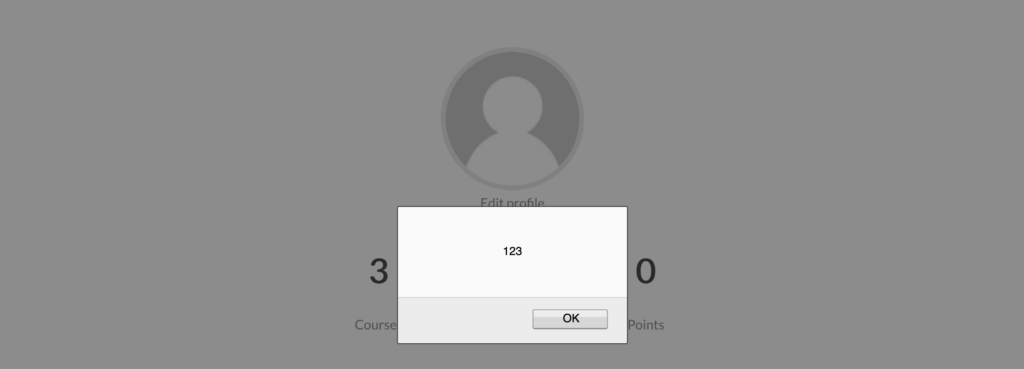
An attacker can modify the above URL and use an advanced payload that could help him/her in performing malicious actions.
Timeline
- Vulnerability reported to the LearnDash team – January 14, 2020
- LearnDash version 3.1.2 containing the fix released – January 14, 2020
Recommendation
It is highly recommended to update the plugin to the latest version (>= 3.1.2). If you are using the Astra Security Suite, you are protected against this vulnerability.





