WPForms Plugin version 1.5.8.2 and below were found to be vulnerable to authenticated stored XSS while I was auditing the plugin. WPForms version 1.5.9 with improved data sanitization was released on March 5, 2020.
Summary
WPForms is a popular WordPress forms plugin with over 3 million active installations. It was found to be vulnerable to authenticated Cross-Site Scripting (XSS) vulnerability. XSS is a type of vulnerability that can be exploited by attackers to perform various malicious actions such as stealing the victim’s session cookies or login credentials, performing arbitrary actions on the victim’s behalf, logging their keystrokes and more.
Vulnerability
The Form Description and Field Description fields in the WPForms plugin’s Form Builder module was found to be vulnerable to stored XSS, as they did not sanitize user given input properly.
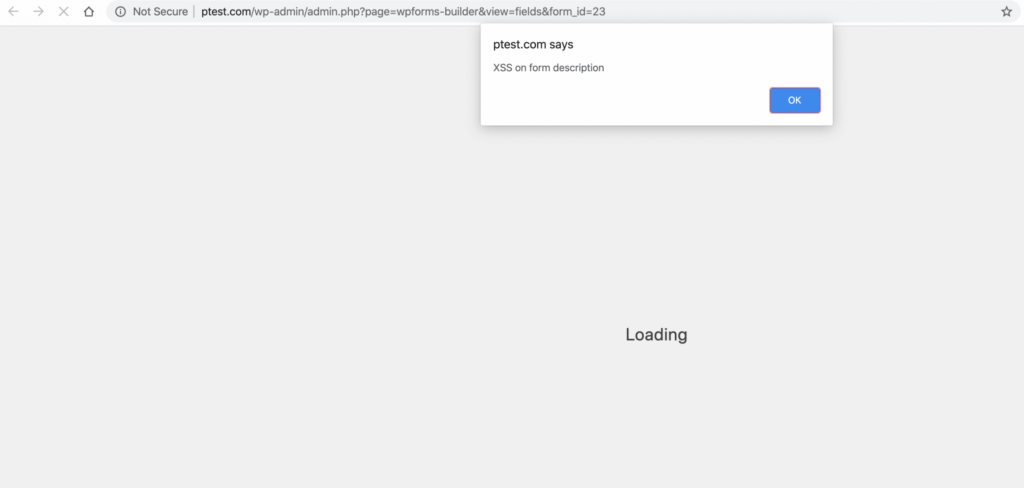
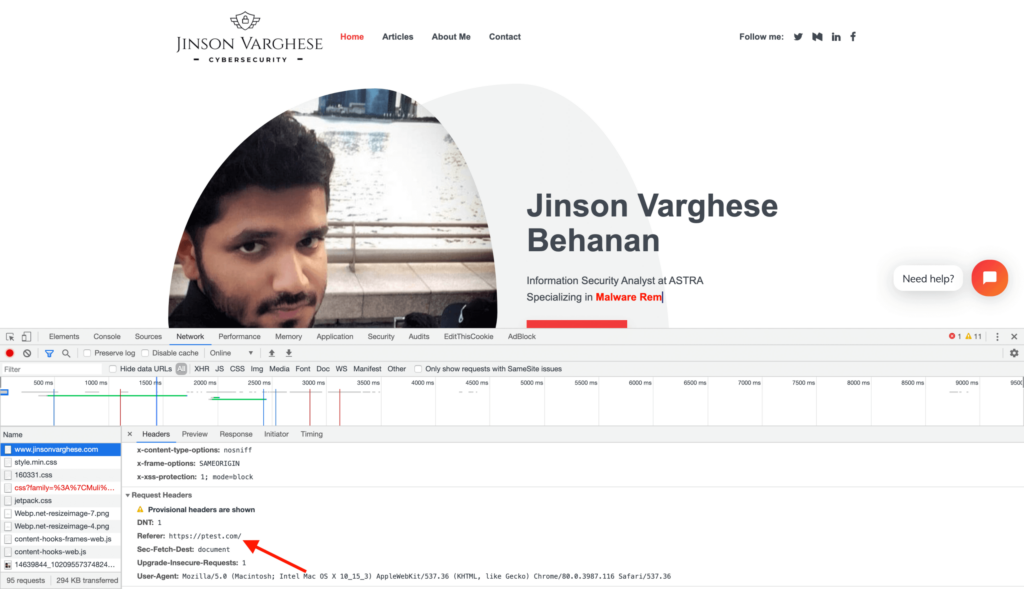
While they do not pose high security threat being an authenticated XSS vulnerability, we were able to confirm that these can be potentially exploited by an attacker to perform malicious actions on a WordPress multisite installation to have a super admin’s cookies sent to the attacker or redirect the super admin (as shown below) to another domain, for example, a phishing page designed to show that they have been logged out and would need to log back in, thus compromising their credentials.
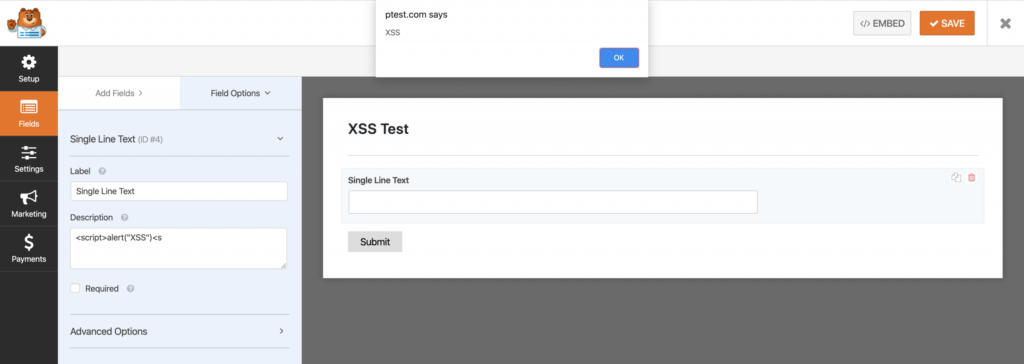
We were further able to find that the form builder’s “preview” function was also vulnerable to reflected XSS.
Timeline
- Vulnerability reported to the WPForms team – February 18, 2020.
- WPForms version 1.5.9 containing the fix to the vulnerability released – March 5, 2020.
Recommendation
It is highly recommended to update the plugin to the latest version.